Capturing the Flag: A Recap of OSDCTF'22
Last week, we had the pleasure of organizing our first-ever CTF competition with over 100 participants. It was a unique experience, especially since our college was hybrid due to the infamous COVID-19 pandemic. To shake things up and add some excitement to daily classes, I decided to volunteer for the annual Open Source Developers Hackathon (OSDHACK'22) and pitch the idea of hosting a CTF event. Thankfully, the organizers were on board and gave us the green light to bring our CTF vision to life. It was a magical experience, and we couldn’t have done it without the support of the Open Source Developers community and our amazing participants.
The Horcrux of the Matter
To add a touch of mystery and intrigue, we decided to theme our CTF event around the concept of horcruxes from the Harry Potter series. For those unfamiliar with the term, a horcrux is an object in which a Dark Wizard has hidden a fragment of their soul for the purpose of attaining immortality. In the context of our CTF, we used a tool called Horcrux to split and merge files as part of the challenges.
We created a secret portal on the OSDHack website that could be accessed by clicking on the logo five times. This redirected participants to the OSDCTF'22 website, where they would find five challenges waiting for them. Each challenge, when solved, would lead to a flag and a download page where participants could download a file. The goal was for participants to collect all five files and use Horcrux to combine them into a single file, which contained the flag hidden in its metadata. The first four participants to successfully complete the challenges and find the flag would receive prizes (aka “biryani monies.")
Plot Twist
The competition got off to a blazing start, with the first three winners completing the challenges in just two hours! It turns out that the first challenge was a bit too easy and served more as a sanity check. Nonetheless, the competition was a success and the participants seemed to enjoy the challenges.
Challenges
Challenge 1: Wh0 1s Th3 1mp0st3r (OSINT)
Description: Someone in the OSDHack server on Discord has been misusing their administrative rights and left a trail in their bio. Can you find the flag and uncover the identity of the imposter?
Solution: This was a straightforward OSINT challenge. The flag was hidden in the bio of the OSDHack'22 bot account, which was offline at the time of the competition. Participants simply had to scroll through the list of offline users and find the flag.
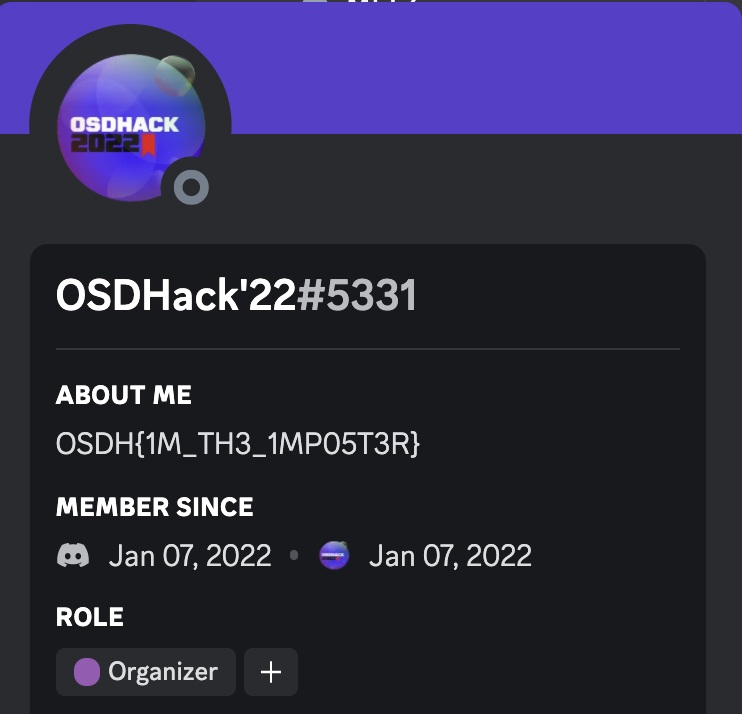
Flag: OSDH{1M_TH3_1MP05T3R}
Challenge 2: T00 Much Cyph3r (Crypto)
Description: Isn’t it too much encrypted ???T95ApKshwrT2mTRnCoN9dkGFSgc
Solution: This challenge was all about cryptography. The flag was encrypted using a combination of alphabetical substitution, ROT13, and Base58. A tool like Cyberchef could be useful for decoding the message.
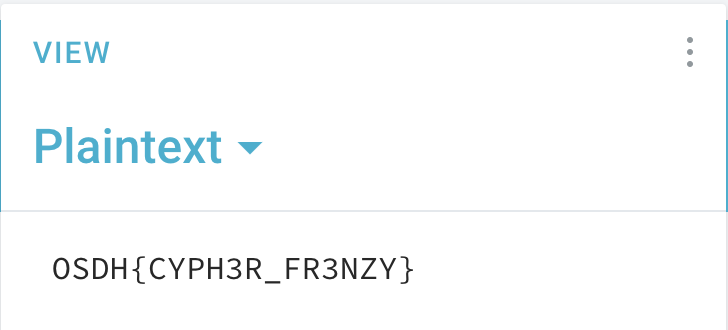
Flag: OSDH{CYPH3R_FR3NZY}
Challenge 3: Security Is Fun in OSDH (OSINT)
Description: To make OSDHACK fun for all, our organizers hired someone from WICK.SECURITY to ensure the event ran smoothly. However, it seems like this person really likes to post pictures and may have made OSDHACK vulnerable.
Solution: This was a popular challenge among participants. The person in question had an Instagram account under the handle wick.security, and one of their posts contained a link to a Rickroll (xD) video. The flag was in the “About Me” section of the video.
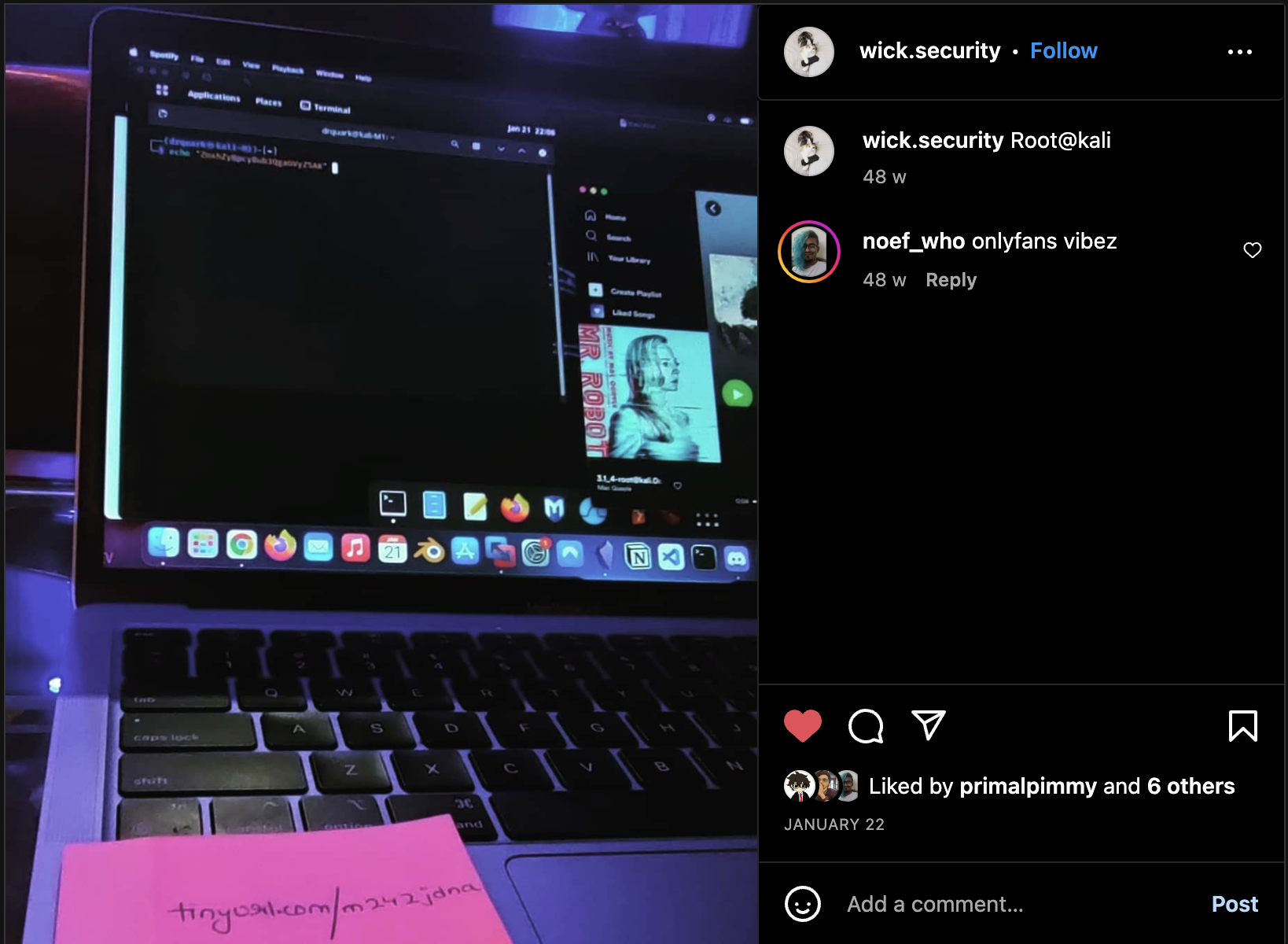
Flag: OSDH{0S1N5TA}
Challenge 4: 4M4Z1NG P1CTUR3 ( TYPE - FORENSICS )
Description - amazing picture ? Hmm this image doesn’t seem to be working.
Solution: This was a simple forensics challenge. Participants just had to change the file extension to .txt to reveal a flag encrypted using ROT13.
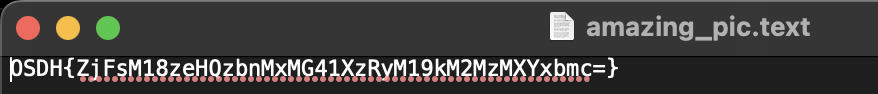
Flag: OSDH{f1l3_3xt3ns10n5_4r3_d3c31v1ng}
Challenge 5: G1T 1S GUD ( TYPE - OSINT )
Description - Are you committed to OSHACK ?? https://osdhackjiit.com/
Solution - In this challenge, participants had to visit the GitHub repository of the OSDHACK website and search through the commit messages to find the flag. It was a simple task for those who were truly committed to solving the challenge.
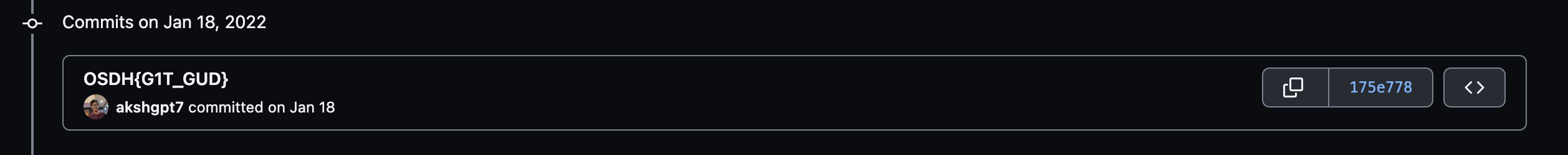
Flag: OSDH{G1T_1S_GUD}
Once all of the challenges were completed, participants had to download the resulting files and use Horcrux to combine them into a single file. The flag was then hidden in the metadata of the final image of Tuxi. With the flag in hand, participants had officially completed the OSDCTF'22.
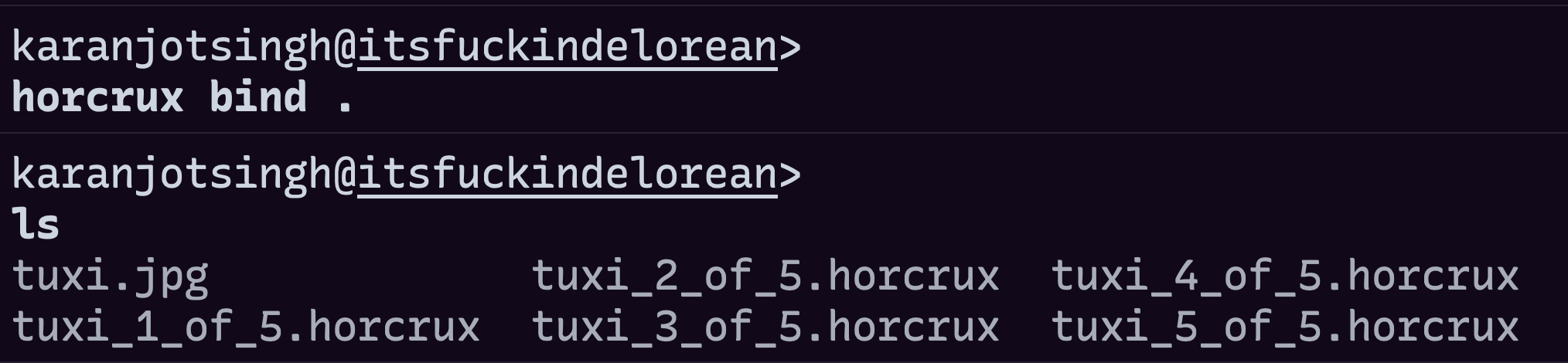

Final Flag: OSDH{the_m3tadata_1s_modified}
The End of a CTF-tastic Adventure
It’s a wrap on the OSDCTF'22, and what a journey it has been! Over 100 participants tested their cybersecurity skills and braved the Horcrux-filled challenges, with the first three winners completing the competition in a speedy two hours.
From deciphering encrypted messages and analyzing Instagram posts to extracting hidden information from image files and searching through commit messages, our CTF competition had a little something for everyone.I want to extend a special thank you to Primal Pimmy and other OSDC Members for helping me organize the event and make it a success. We hope that all of the participants had as much fun as we did organizing the event and that they learned a thing or two along the way.
Congratulations to all of the winners and a big thank you to everyone who participated. We hope you had as much fun solving the challenges as we had creating them.
Until next time, Happy Hacking!